by Jerry Stern
Webmaster, PC410.com
Westminster, Maryland
Reprint from the February 2010 ASPects
Editor’s Note: This article was written for programmers, on how not to look evil, but software consumers will find it helpful in identifying the patterns in malware products. Familiar, generic, and somewhat scary program screens are frequently just plain evil.
Back in the ’90’s, there were regular discussions in the ASP forums on Compuserve about “what to name my product?” These are still happening. Then, the common errors were to American-ize the pronunciation of an abbreviation. For example, using FileManagerEZ, and assuming that it means “File Manager Easy.” Well, in the USA, it does, but elsewhere, it’s “File Manager Eee Zed”, and not quite recognizable.
There were also the endless repeats of name issues for screen savers. The topic frequently became “YASS” for “Yet Another Screen Saver.” There are always overloaded program categories, where it just becomes non-productive to keep making variations on a theme.
These issues still exist. But the web changed everything else, and malware rogue products change everything all over again.
So here is my top five list of stupid software marketing tricks: Do any of these at your own risk. Combine them, and in these days of social networking and website tagging, don’t be surprised if your sites are incorrectly blacklisted by security companies and your products are flagged as malware by non-experts and opportunists.
1) Trying to match the Microsoft style
There are reasons for and against this. Pro: Comfort level for users, and possibly ease of use, if the ribbon bar has the ‘MS Look.’
Con: Lack of innovation. Possible trademark infringement. Boring–users have seen it before; that’s the whole point of copying. Worst, you’re competing against everyone else who copies from other people’s work, including malware authors.
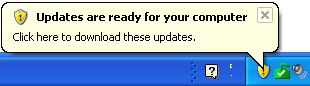
Example: Windows shows a real ‘update’ flag, and a malware program copies the look of Microsoft Windows’ balloon notification messages, and adds a standard message prompt.
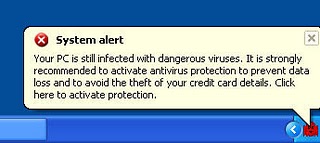
And here is Ghost Antivirus’ fake balloon message:
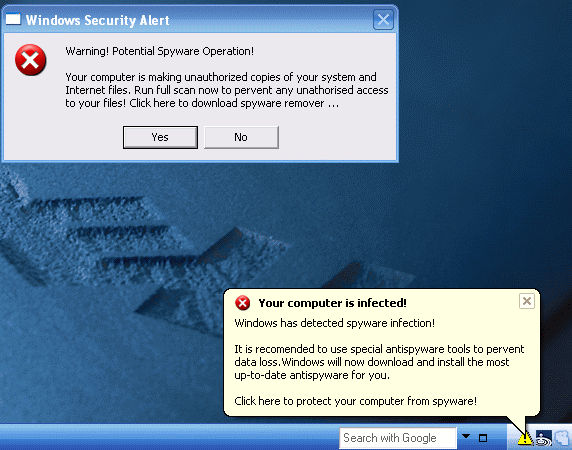
2) Trying to clone another product’s look
Going beyond just copying button styles and interface elements, you could copy the entire product interface, colors, everything except the product name.
There are thousands of examples of this; the malware authors are creating new variations on this many times daily, with different names, but with interfaces copied from Microsoft and many of the well-known security vendors.
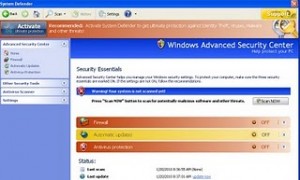
Example: In figure 1, Windows Defender, a real part of Windows Vista. In figure 2, Desktop Security 2010, a clone of Defender that blackmails the user for an online payment for a product that does nothing.
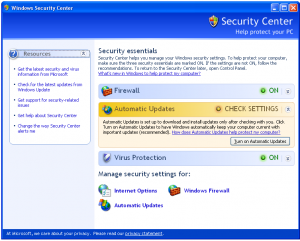
Example: Below, first there is the real Windows Security Center from Windows XP, and below, the main screen of System Defender, another rogue.
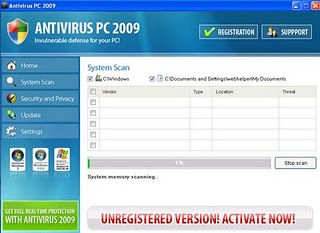
3) Naming your product with a year.
This is showing up in malware rogues consistently. Why? Well, weak trademarks are very difficult to search for online. “Desktop Security 2010” In the short period of time after these products are pushed out, but not yet blocked by anti-malware programs, it’s a big advantage if the product name is vague. After a few days, it won’t matter; the name changes, a few detection details change, and a new ‘product’ takes over.
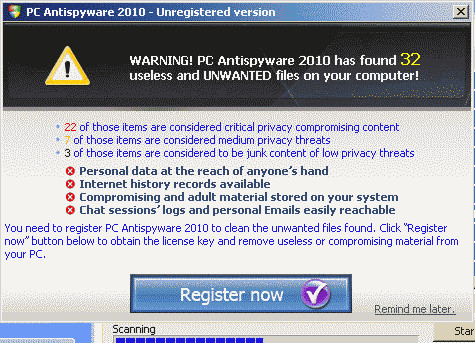
4) Scary Prompts

When PC owners see scary prompts, they rarely reach for a credit card. They reboot the computer, or if they’re in Westminster, Maryland they call me, or they drag the PC to the nearest GeekOnPatrol, or whatever the local electronics store has named their crew of nerds. It’s a good way to get wiped off the computer. The rogue antimalware crowd can make money that way by mass distribution through drive-by downloads, trojan downloads of fake receipts, and every other trick they can come up with. But scary doesn’t work for real companies; we sell software based on comfort levels, not on fear.
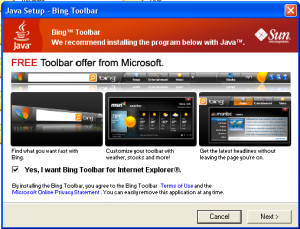
5) Piggy-Back Rides
One program installer should setup one program. There are no exceptions if you’re trying to sell non-trivial software that will eventually involve updates, support, add-on sales, or new versions. If your program was installed as a checkbox on some startupware, or your program installs other companies’ stuff, what does that say about your program?
Don’t look like malware. Use strong trademarks that don’t sound like anybody else’s products, don’t look like other products, and don’t share their downloads with other products. Your software’s identity should be unique. Familiar is both boring and dangerous territory. Be creative, be one of a kind, and your software won’t look evil by association with malware.
Jerry Stern was the editor of ASPects from 1997 to 2015, the ASP’s Coordinator of Anti-Spyware Operations, runs PC410.com in Carroll County Maryland, and is online at www.sciencetranslations.com.
